Member-only story
Taints and Tolerations — Kubernetes
Taints and Tolerations the main goal of this feature was to prevent unwanted pods from being scheduled on some particular nodes.
Kubernetes also used this feature to prevent pods from being scheduled on the master node and to ensure the master node was free from taking on workloads.
Taints and Tolerations are used to set restrictions on what pods can be shared on that node.Taints are generally applied on nodes to prevent unwanted scheduling, tolerations are applied on pods to allow them to be scheduled on nodes that have taints.
buymeacoffee ☕ 👈 Click the link
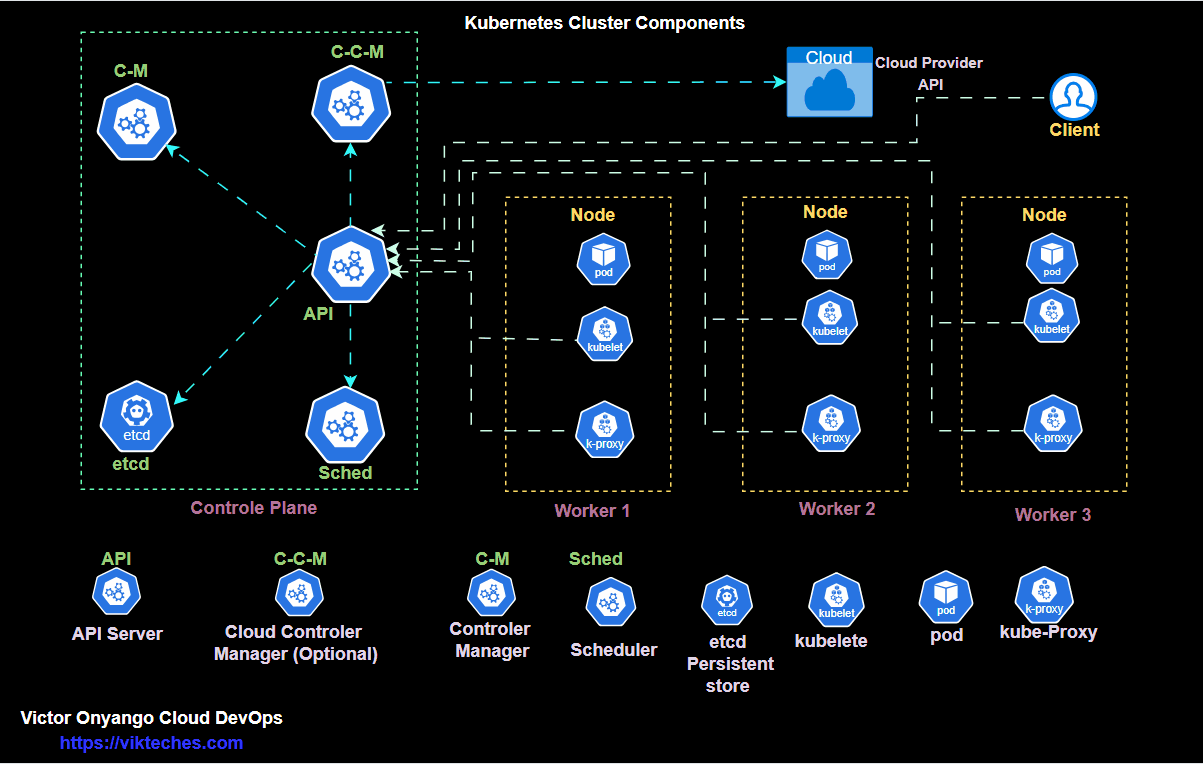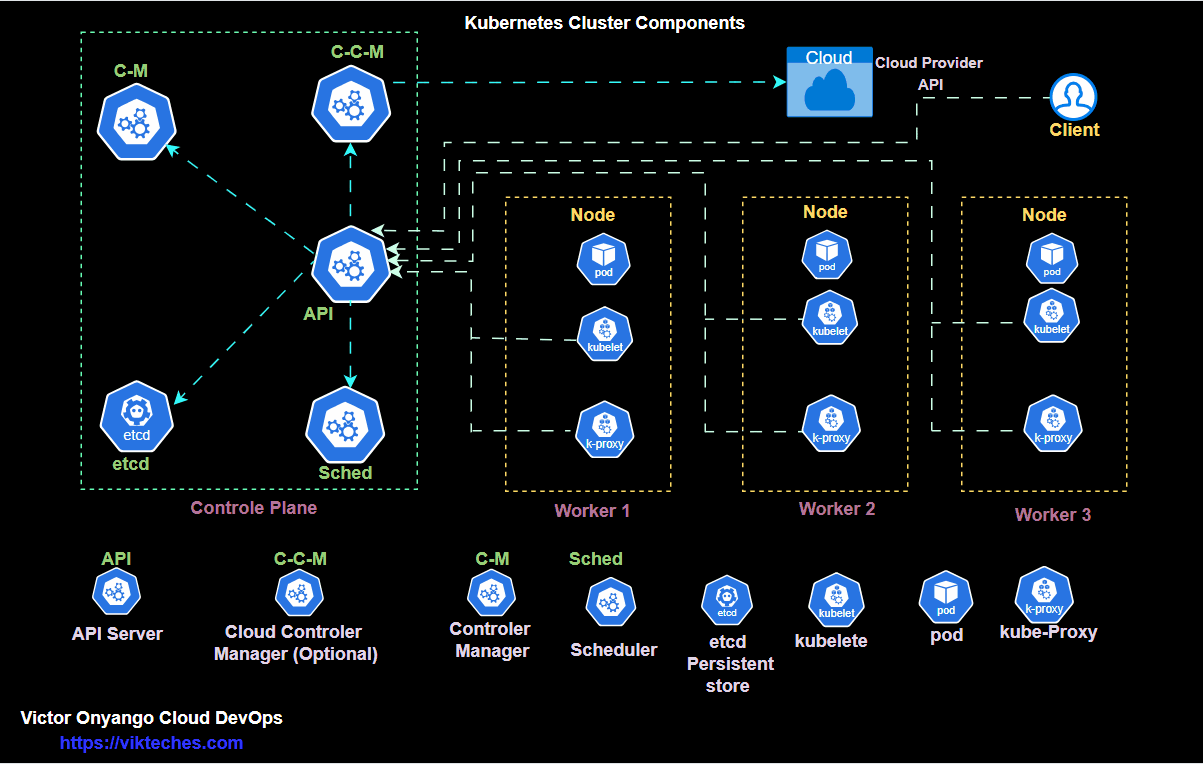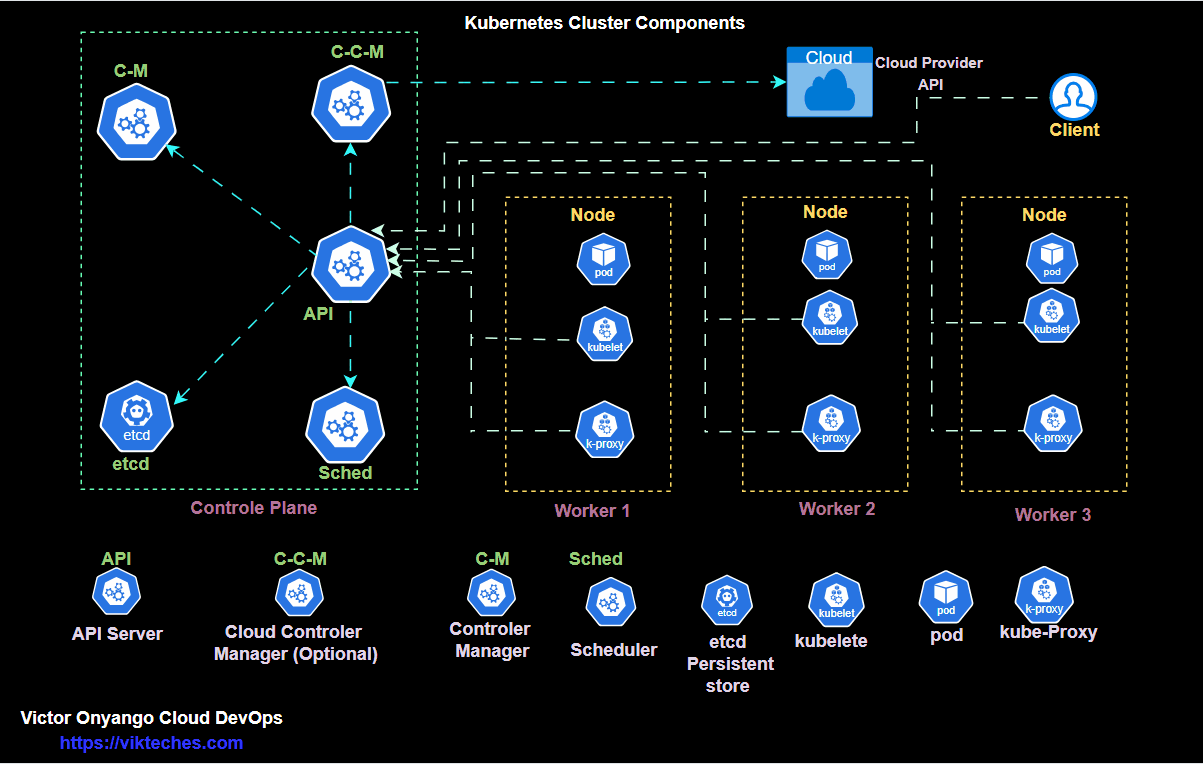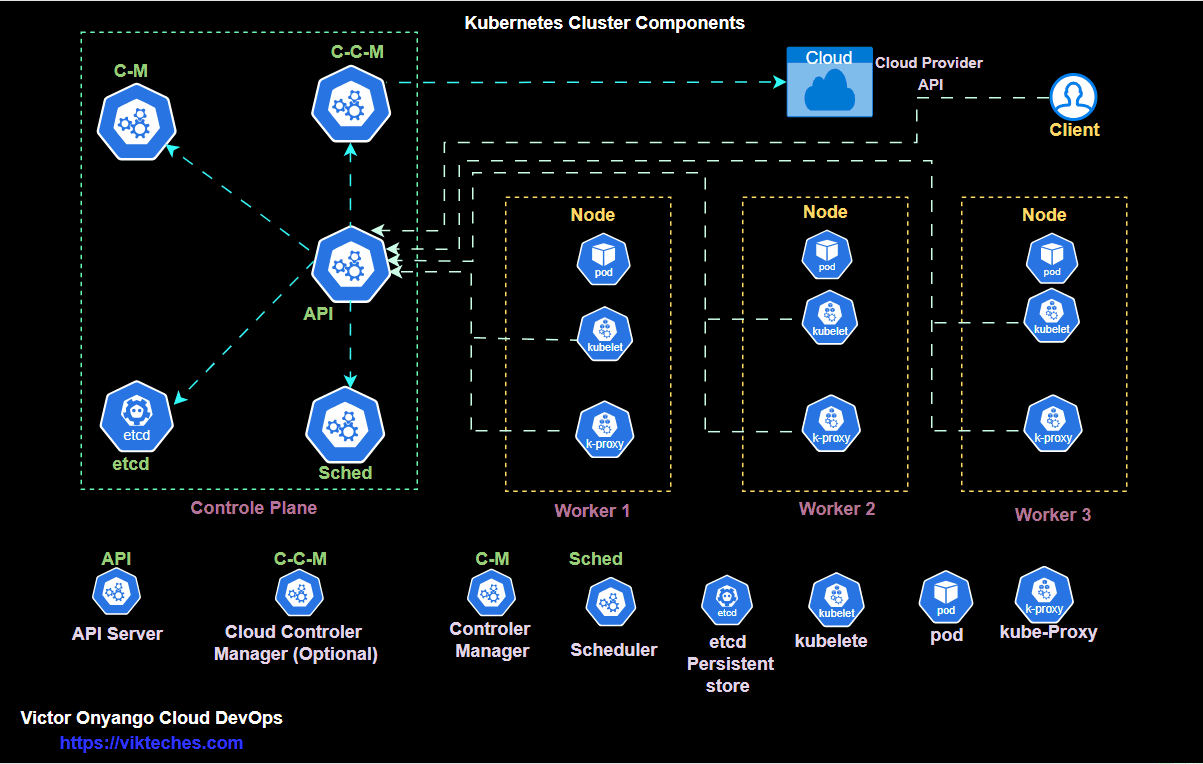
What is Scheduling?
Scheduling isn’t about timing, but about ensuring that pods are matched to nodes.
When we create a pod, the scheduler in the control plane looks at the nodes and verifies available resources and other conditions before assigning a pod to the nodes.
If there are no errors during the verification, the pod will be scheduled on the node.
Tainting — Node
To taint a node, specify the node name to taint followed by a taint itself which is a key-value pair.
Taint-effect defines what would happen to the PODs if they do not tolerate the taint.
kubectl taint nodes node-name key=value:taint-effect